A good tweet by @SwiftOnSecurity reminded me of one of a basic way we can detect compromised Microsoft accounts: monitoring new email rules.
Creation of new inbox rules is one potential sign of account compromise. Monitoring them is one way to stay on top of potential security incidents.
How attackers use inbox rules
Attackers leverage inbox rules in a couple of ways. Deleting incoming emails from the help desk is one common technique. An attacker might not know the email address of your actual help desk, but they will create inbox rules that delete anything with certain phrases (“Service Now,” “ticket,” “support,” etc.). This helps the attacker avoid detection and maintain access to the account.
When it comes to leveraging this compromised account, the attacker’s best bet is to reach out to contacts in a user’s address book. This often comes in the form of a phishing email, or another type of scam (the gift card scam is popular at the moment).
Inbox rules help an attacker manage responses to their malicious campaign and keep them out of sight of the compromised user.
In the past, a common tactic was to simply forward a user’s email elsewhere. Microsoft has provided guidance on disabling external auto-forwarding, and has disabled this by default. Do not allow users to automatically forward to an external mailbox!
Detecting inbox rule creation
Detecting new inbox rules is fairly straightforward. You can turn on forwarding/redirect alerts on in the policies section of the Security and Compliance Center:
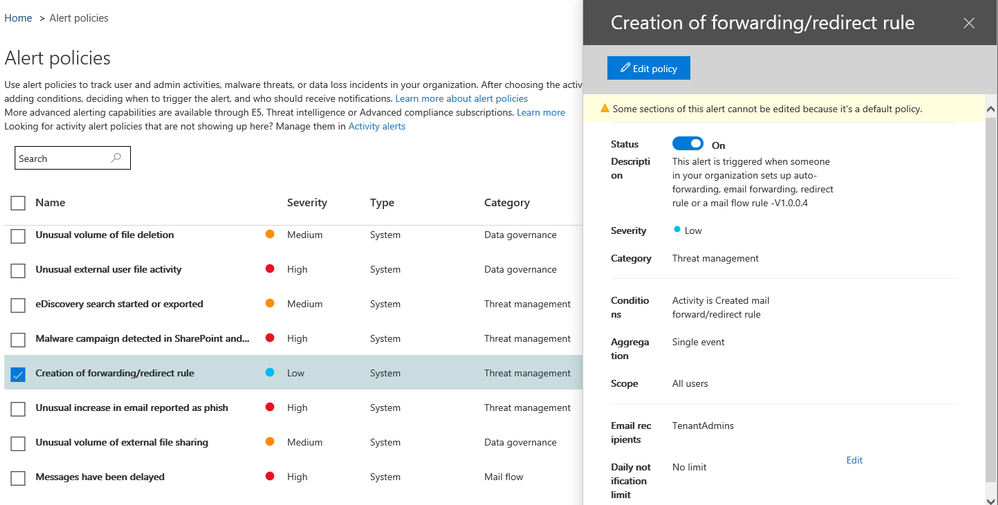
Depending on the size of the organization and sophistication of users, this alert could potentially generate false positives. As of this writing, there are not many options for tuning. It would be great to be throttle alerts for users who make new rules often.
Note that the above only works for forwarding/redirect rules. It will not alert on every inbox rule created. So if an attacker does create a rule to delete certain emails, this will not detect that.
To monitor for all new inbox rules, there are options within Microsoft Cloud App Security (MCAS). Of course, that costs money. I’m not able to test this at the moment, but you should be able to create a policy based on the New-InboxRule Powershell cmdlet.
MCAS also has rules that will overlap with the forwarding rule mentioned earlier. That policy is called “suspicious inbox forwarding.”
Final notes
A later tweet clarified that this is not just for those with M5/E5 licenses, this is possible using standard alerting policies in the Microsoft Security and Compliance Center.
Be aware this alert only applies to rules created by Outlook on the web or via Exchange Online Powershell. This particular rule does not alert on a user creating inbox rules on an executable Outlook client. This improves the signal-to-noise ratio, as a compromised account is likely to be leveraged via the web or Powershell.
